How do hackers use metadata?
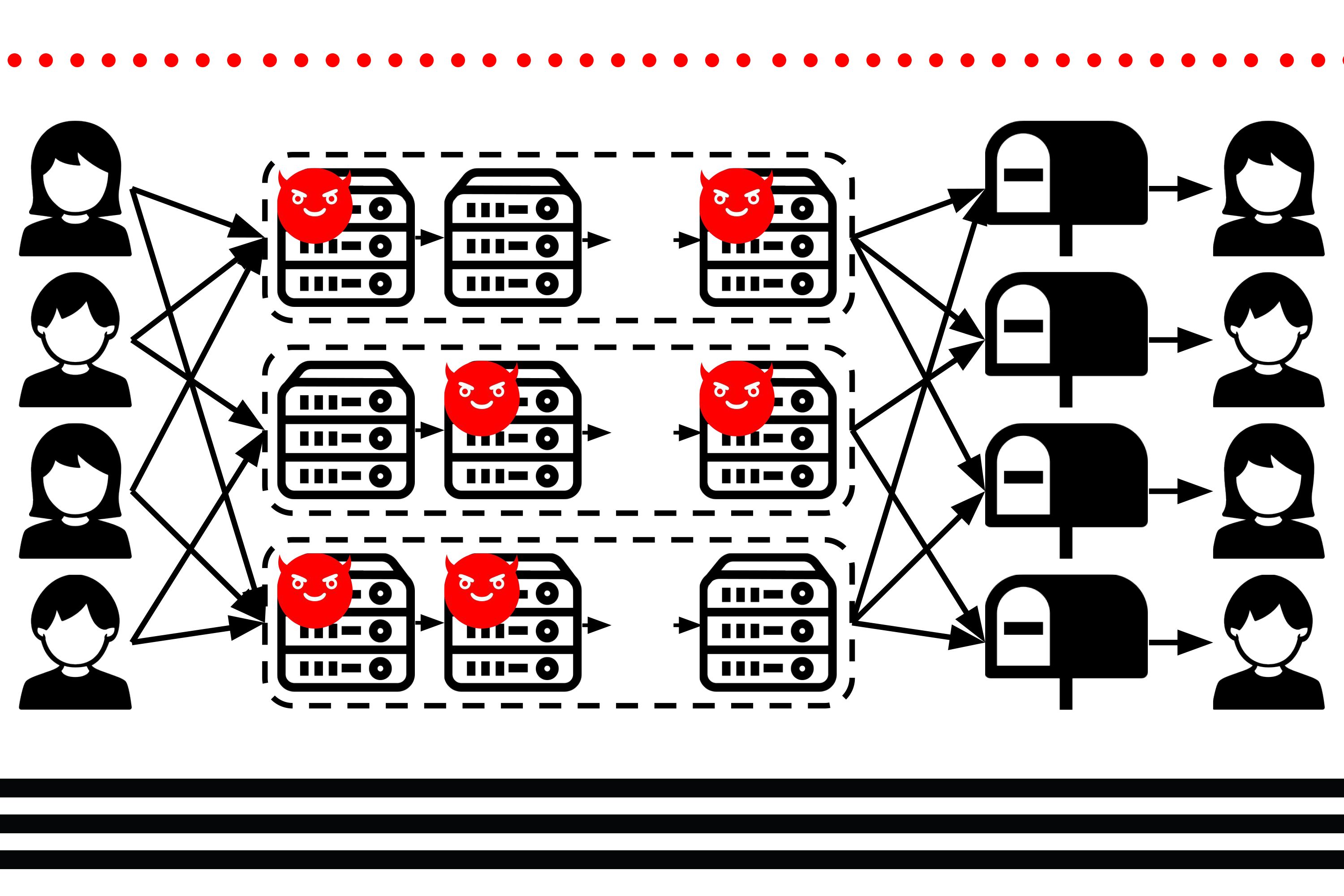
How do hackers use data maliciously
Hackers create malicious apps that can siphon personal information from your device when you download or use the apps. Cybercriminals set up fake public Wi-Fi networks to lure and redirect people to malicious websites where they can steal personal information.
How do hackers gain access to your data
One way is to try to obtain information directly from an Internet-connected device by installing spyware, which sends information from your device to others without your knowledge or consent. Hackers may install spyware by tricking you into opening spam email, or into “clicking” on attachments, images, and links in …
How do hackers search for information
Specialized IoT search engines like Rapid7 and MITRE track vulnerabilities known to specific devices. Using yet another IoT search engine like Shodan and ZoomEye, hackers can find devices connected to the internet, geolocation, port/operating system, services/host, and IP address.
What data are hackers looking for
Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft, such as using the victim's credit card or taking loans in their name.
Can hackers see my screen
Can a hacker access my computer camera, microphone, and screen Yes. Cybercriminals use malware like spyware to remotely access and control your camera, microphone, and screen. In fact, malicious actors often use camera and microphone recordings to blackmail people.
What technique do hackers use to steal information
The attacker uses a virus, Trojan, and other malicious code and installs them on the victim's computer to get unprivileged access. Virus and other Trojans keep sending data to the hacker regularly and can also perform various tasks on the victim's system like sniffing your data and diverting traffic etc.
What do most hackers want
Stolen personal information is fuel for identity theft
Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft, such as using the victim's credit card or taking loans in their name.
Can hackers see your private searches
While someone using your device won't be able to see your browsing history, incognito mode won't be able to stop hackers and identity thieves in their tracks.
Who gets hacked the most
Corporate and Small-Business Hacking Statistics
Small businesses are the primary target of cyber attacks, and hackers show no sign of stopping. Small businesses account for 43% of cyber attacks annually, and 46% of cyber attacks were small businesses with 1,000 or fewer employees.
What do hackers want the most
Stolen personal information is fuel for identity theft
Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft, such as using the victim's credit card or taking loans in their name.
Can hackers see and hear you
Yes, different types of hackers may be able to hear you if they've gained access to your phone's camera and microphone.
Can hackers mirror my phone
Mirroring applications leverage screen-streaming technology to remotely view anything occurring on your phone in realtime. This means that any texting, browsing or other activities can be viewed by the hacker. The real kicker is that mirroring apps are often installed without the victim's knowledge.
What is the most used hack
Phishing is the most common hacking technique.
How many ways can you hack data illegally
Here are five ways hackers can access your systems, view your files, and steal your data if you're not careful.Malware. One of the most well-known data theft attack methods in existence is malware.Compromised Passwords.Unsecured Internet Connections.Ransomware.Phishing and Social Engineering.
What hackers love most
Let's delve right in.Vulnerabilities in Your System. Hackers love nothing more than finding vulnerabilities in your system.Lack of Security Awareness. The human factor is often the weakest link in any organization's security.Unencrypted Data.Data That's Not Backed Up.Lack of Two-Factor Authentication.
Why are hackers rich
Ethical hackers, can make millions when companies pay them for breaking past their security, exposing their vulnerabilities and checking the security of their IT systems.
Can hackers see deleted history
Cybercriminals and hackers can gain access to personal information stored in your computer even after you think you've deleted the files.
Is it safe to go incognito
Is incognito mode safe to use There's no harm in using incognito mode. While it doesn't protect your privacy as much as many may think (but now you know better), it is safe to use as long as your browser is secure and up to date. However, incognito mode doesn't guarantee any more security than the usual browsing mode.
How rare is it to be hacked
How many people get hacked a year There isn't concise data on how many people get hacked a year. However, considering there are around 2,200 cyberattacks per day, that could equate to more than 800,000 people being hacked per year.
What is the top 1 hacker
Kevin Mitnick holds the title as the world's most famous hacker ever, with this title dating back to 1995 by the US Department of Justice. Kevin Mitnick started hacking at an early age.
Can hackers read your screen
Spyware is literally a tool intended to spy on your phone or computer activity. Remote access tools: Hackers can use remote access tools to take control of a victim's device and use it to view or control the victim's screen.
Can hackers see what I’m doing on my phone
Hackers can also use keyloggers and other tracking software to capture your phone's keystrokes and record what you type, such as search queries, login credentials, passwords, credit card details, and other sensitive information.
What is the hardest device to hack
Most Secure PhonesBittium Tough Mobile 2C. The first device on the list of most secure Phones is the Bittium Tough Mobile 2C.K-iPhone – One of the most secure Phones.Most secure Phones – Solarin From Sirin Labs.Among the most secure Phones – Purism Librem 5.Sirin Labs Finney U1.
What was the worst hack ever
August 15: Saudi Aramco is crippled by a cyber warfare attack for months by malware called Shamoon. Considered the biggest hack in history in terms of cost and destructiveness. Carried out by an Iranian attacker group called Cutting Sword of Justice. Iranian hackers retaliated against Stuxnet by releasing Shamoon.
Is IT legal to be a hacker
So, is Hacking legal No, hacking cannot be regarded as legitimate if it is done without the owner's permission. One could face criminal charges and a prison sentence if proven guilty of hacking without permission. However, there are some legal issues associated with hacking.